Specialists from foreign countries and other users started to seek advice after reading this article. Understand A Breachs Impact On Your Organization With In-Depth Root Cause Discovery.

How Does Digital Forensics Differ From Common Data Recovery Digital Forensics V S Common Data Recovery Ecs Biztech Ltd
Digital forensics refers to the process of protecting and analyzing the collected data.

. True or False2 The triad of computing security includes. The data can be on a computer system or a piece of hardware. The triad of computing security includes which of the.
Digital forensics and data recovery refer to the same activities. Digital Forensics and data recovery refer to the same activities. Turns out not all of you.
Data forensics also know as computer forensics refers to the study or investigation of digital data and how it is created and used. Ad Empower Your Post-Breach Actions Recover Control With LIFARS SecurityScorecard. Digital forensics is a part of Ethical hacking.
Regularly data recovery manages one disk drive or the data from one system. View Ch1Reviewdocx from CS 307 at Limestone College. 2 The triad of computing security includes which of the following.
View attachment_1 3pdf from MATH 123A at University of Lagos. Data structures are central to computer science and consequently bear importance to digital forensics. Digital Forensics and data recovery refer to the same activities.
Digital forensics and data recovery refer to the activities. A Detection response and. Police in the United States.
The data recovery house will have its own norms and methodology. Digital Forensics and data recovery refer to the same activities. Re ie Q e ion 1.
False Data collected before an attorney issues a memo for an attorney-client privilege case is protected under the. View Week 2 Homework Questionsdocx from INFO 316 at Ramapo College Of New Jersey. Digital forensics and data recovery refer to the activities.
Data recovery typically refers to the process of salvaging data from media. Digital forensics and data recovery refer to the same activities. View full document.
Raw format proprietary format and advanced. This data is used by law enforcement as. The purpose of maintaining a network of.
Data recovery is also a term some people use interchangeably though mistakenly with computer or digital forensics. False digital forensics is analyzing and documenting data found on a computer in order to aid a criminal. Digital forensics and data recovery refer to the same activities.
Understand A Breachs Impact On Your Organization With In-Depth Root Cause Discovery. COMP2310 Digital Forensics My Assignment Tutor. The extraction function is the recovery task in a computing investigation and is.
Data forensics is a broad term as data forensics. Data Acquisition the first task in digital forensics investigations involves making a copy of the original drive. 1 Digital forensics and data recovery refer to the activities.
Digital forensics and data recovery refer to the same activities. Study Material for First in Class Multi Choice Continuous Assessment Digital Forensics study guide by Ra_Dian includes 50 questions covering vocabulary terms and more. It deals with Data Recovery techniques and data manipulation tracking down the source of images videos and mp3s uploaded on the web.
Ad Empower Your Post-Breach Actions Recover Control With LIFARS SecurityScorecard. Digital forensics and data recovery refer to the same activities. Name the three formats for digital forensics data acquisitions.
Police in the United States. Data Structures Data Organization and Digital Evidence. Guide to Computer Forensics and Investigations with DVD 5th Edition Edit edition Solutions for Chapter 1 Problem 1RQ.
Is data recovery possible after ransomware.

Pdf Data Recovery Function Testing For Digital Forensic Tools Semantic Scholar
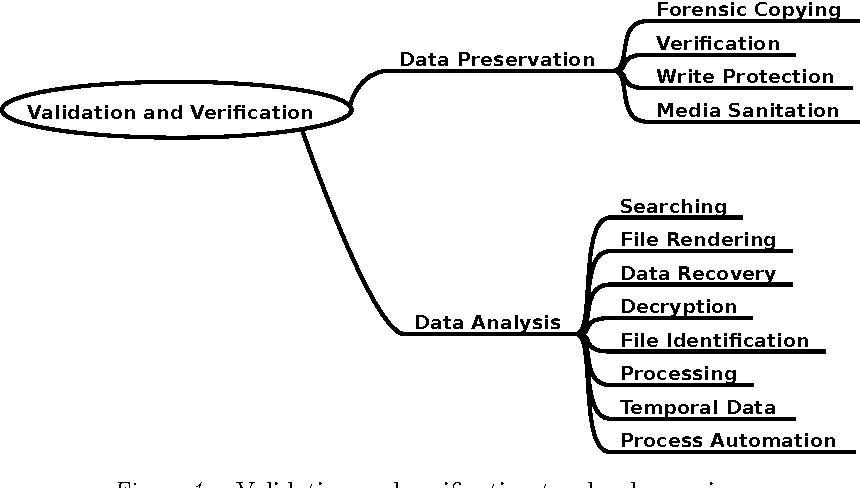
Pdf Data Recovery Function Testing For Digital Forensic Tools Semantic Scholar
Pdf Data Recovery Function Testing For Digital Forensic Tools

0 Comments